Dynamics CRM Access Checker: 7 Powerful Tools to Unlock Security Insights
Navigating the complexities of user access in Dynamics CRM can be daunting. With data security at stake, a reliable Dynamics CRM access checker is essential for maintaining control, compliance, and operational efficiency across your organization.
Understanding Dynamics CRM Access Checker: The Foundation of Secure CRM Management

A Dynamics CRM access checker is more than just a diagnostic tool—it’s a strategic asset for organizations relying on Microsoft Dynamics 365 Customer Engagement (formerly CRM) to manage customer relationships, sales pipelines, and service operations. At its core, this tool enables administrators and security analysts to verify, audit, and manage user permissions across the CRM environment.
Microsoft Dynamics 365 is built on a role-based security model, where access to data and functionality is governed by security roles assigned to users. However, as teams grow and roles evolve, it becomes increasingly difficult to manually track who has access to what. This is where a Dynamics CRM access checker comes into play—offering visibility into user privileges, detecting permission conflicts, and ensuring compliance with internal policies and external regulations like GDPR or HIPAA.
According to Microsoft’s official documentation on security roles, security roles define the set of privileges and access levels that determine what a user can do within the system. Without a proper access checker, organizations risk data breaches, unauthorized modifications, or inefficient troubleshooting of access-related issues.
What Is a Dynamics CRM Access Checker?
A Dynamics CRM access checker refers to any tool, script, or built-in feature that allows system administrators to inspect and validate user access rights within a Dynamics 365 environment. This includes checking which security roles are assigned, what privileges those roles grant, and how access is inherited through teams, business units, and hierarchies.
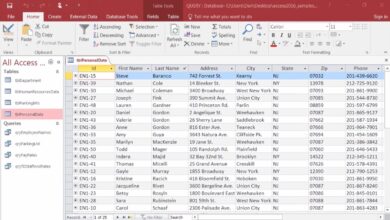
These tools can be native features within Dynamics 365, such as the Security Analyzer or User Access Checker in the Power Platform Admin Center, or third-party solutions designed to provide deeper insights and reporting capabilities. Some organizations also develop custom PowerShell scripts or use SQL queries (in on-premises deployments) to extract and analyze access data.
- It identifies who has access to specific records, entities, or modules.
- It reveals potential over-privileged users or permission gaps.
- It supports compliance audits by generating access reports.
“Effective access management is not just about locking down data—it’s about enabling the right people to do the right things at the right time.” — Microsoft Dynamics 365 Security Best Practices Guide
Why Access Control Matters in Dynamics CRM
In today’s data-driven business landscape, CRM systems house some of the most sensitive information—customer contact details, financial data, sales forecasts, and service histories. Uncontrolled access can lead to data leaks, insider threats, or regulatory penalties.
A Dynamics CRM access checker ensures that access is aligned with the principle of least privilege: users should only have the minimum level of access necessary to perform their job functions. This reduces the attack surface and limits the damage from compromised accounts.
For example, a sales representative should not have access to financial reporting modules unless explicitly required. Similarly, a customer service agent should not be able to modify pricing configurations. Without a systematic way to audit these permissions, such misconfigurations can go unnoticed for months.
Key Features of an Effective Dynamics CRM Access Checker
Not all access checking tools are created equal. To be truly effective, a Dynamics CRM access checker must offer a comprehensive set of features that go beyond simple role listing. The best tools provide real-time insights, historical tracking, and actionable recommendations.
Organizations evaluating access checkers should look for solutions that integrate seamlessly with their existing Dynamics 365 deployment—whether cloud-based (SaaS), on-premises, or hybrid. The tool should also support both model-driven and canvas apps if the organization uses Power Apps alongside Dynamics.
Microsoft’s Power Platform Admin Center already includes basic access auditing tools, but many enterprises require more advanced functionality. Third-party tools like Inogic’s Security Manager or PowerObjects’ Power365 Security extend these capabilities significantly.
Real-Time Access Auditing and Reporting
One of the most critical features of a Dynamics CRM access checker is the ability to generate real-time reports on user access. This includes not only current role assignments but also effective permissions—what a user can actually do when role inheritance, team memberships, and business unit hierarchies are taken into account.
For instance, a user might be directly assigned a ‘Sales Representative’ role but also belong to a team that has been granted additional privileges. A good access checker will calculate the net effect of all these assignments and present a clear picture of the user’s total access rights.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
These reports can be scheduled automatically and exported to PDF or Excel for audit purposes. Some tools even allow you to compare access rights across different points in time, helping track changes and identify unauthorized modifications.
- Generate user access summaries by role, team, or business unit.
- Export audit trails for compliance documentation.
- Compare access configurations before and after system updates.
Role Conflict Detection and Overlap Analysis
As organizations scale, users often accumulate multiple security roles—sometimes unintentionally. This can lead to role conflicts, where overlapping privileges create security risks or operational inefficiencies.
A Dynamics CRM access checker with role conflict detection can identify when a user has been assigned roles that grant conflicting permissions—such as one role allowing record deletion and another restricting it. It can also highlight cases where users have redundant roles, making it easier to streamline access and reduce complexity.
For example, if a user has both ‘Marketing Manager’ and ‘Sales Manager’ roles, the access checker might flag that both roles include ‘Read’ access to Leads, suggesting an opportunity to consolidate permissions. This not only improves security but also simplifies future role management.
“Over 60% of security incidents in CRM systems stem from misconfigured user roles and excessive permissions.” — Gartner, 2023 CRM Security Trends Report
Top 7 Dynamics CRM Access Checker Tools in 2024
Choosing the right Dynamics CRM access checker can make a significant difference in how efficiently and securely your organization manages its CRM environment. Below is a curated list of the top seven tools available in 2024, each offering unique capabilities for access auditing, role management, and compliance reporting.
These tools range from free Microsoft-native utilities to premium third-party platforms with advanced analytics and automation features. The selection depends on your organization’s size, deployment model, compliance requirements, and technical expertise.
1. Microsoft Power Platform Admin Center (Free)
The Power Platform Admin Center is Microsoft’s official portal for managing Dynamics 365 and Power Apps environments. It includes a built-in user access checker that allows administrators to view role assignments, audit recent access changes, and monitor user activity.
While not as feature-rich as dedicated tools, it provides essential functionality for small to mid-sized organizations. You can filter users by role, export access lists, and review sign-in logs. It integrates directly with Azure Active Directory, enabling seamless identity management.
One limitation is that it doesn’t provide deep insights into effective permissions or role conflicts. However, for basic access verification, it’s a reliable starting point. Learn more at https://admin.powerplatform.microsoft.com.
- Free to use for all Dynamics 365 customers.
- Direct integration with Azure AD and Microsoft 365.
- Real-time user access monitoring.
2. Inogic Security Manager for Dynamics 365
Inogic’s Security Manager is a powerful third-party tool designed specifically for Dynamics 365 security auditing. It offers a comprehensive Dynamics CRM access checker with advanced reporting, role comparison, and permission analysis features.
The tool provides a visual interface for exploring user roles, team memberships, and business unit hierarchies. It can generate detailed access reports, highlight permission gaps, and even simulate role changes before applying them.
One standout feature is its ‘Access Preview’ mode, which lets administrators see exactly what a user can access without logging in as them—eliminating the need for impersonation. It also supports bulk role assignments and automated compliance checks.
Visit Inogic’s official site for pricing and trial options.
- Visual role and access mapping.
- Bulk role management and automation.
- Compliance-ready audit reports.
3. PowerObjects Power365 Security
PowerObjects, a Microsoft Gold Partner, offers Power365 Security—a robust solution for managing access in complex Dynamics 365 environments. It excels in large enterprises with multiple business units and hybrid deployments.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
The Dynamics CRM access checker component allows administrators to drill down into individual user permissions, detect orphaned roles, and enforce role-based access control (RBAC) policies. It also includes a ‘Security Health Check’ feature that scans the entire environment for common misconfigurations.
Power365 Security integrates with existing IT service management (ITSM) tools and supports automated workflows for role approval and deprovisioning. This makes it ideal for organizations with strict change management processes.
More information is available at PowerObjects’ Power365 Security page.
- Automated security health checks.
- Integration with ITSM and HR systems.
- Role lifecycle management.
4. CRM Perfection’s Access Analyzer
CRM Perfection offers a lightweight yet effective access analysis tool tailored for Dynamics 365 online environments. The Access Analyzer focuses on simplicity and speed, making it ideal for consultants and managed service providers who need to perform quick audits.
It allows users to select a specific record or entity and instantly see who has access to it—based on roles, teams, sharing, and direct privileges. This ‘reverse lookup’ capability is particularly useful when troubleshooting access issues.
While it lacks some of the automation features of larger platforms, its intuitive interface and fast response times make it a favorite among Dynamics CRM consultants. It’s available as a managed solution that can be installed directly into your Dynamics 365 environment.
- Fast record-level access lookup.
- Easy installation as a managed solution.
- Ideal for consulting and audit engagements.
5. XrmToolBox – Security Tools Plugin
XrmToolBox is a free, open-source toolkit used by thousands of Dynamics 365 developers and administrators. Among its many plugins is the ‘Security Tools’ extension, which functions as a powerful Dynamics CRM access checker.
This plugin allows users to view all security roles, compare role differences, and analyze user access in detail. It also includes a ‘Who Can Access This Record?’ feature that mimics the behavior of commercial tools at no cost.
Because XrmToolBox is community-driven, it receives regular updates and new features. However, it requires technical knowledge to install and use, making it better suited for IT professionals than business users.
Download it from https://www.xrmtoolbox.com and search for the Security Tools plugin.
- Free and open-source.
- Highly customizable with plugins.
- Used by Dynamics professionals worldwide.
6. DataVerse Security Analyzer (Preview)
Microsoft is currently developing a next-generation security analysis tool for the DataVerse platform, which underpins Dynamics 365. The DataVerse Security Analyzer is currently in preview and promises to deliver deep, AI-powered insights into access patterns and potential risks.
This tool will go beyond static role checking by analyzing user behavior, identifying anomalous access patterns, and recommending role optimizations. For example, it might detect that a user with ‘Read-Only’ access is frequently attempting to edit records—indicating a potential misalignment between role design and job function.
While still in early stages, the DataVerse Security Analyzer represents the future of Dynamics CRM access checking—moving from reactive auditing to proactive security intelligence.
Stay updated via the Microsoft Power Platform Roadmap.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
- AI-driven access pattern analysis.
- Behavior-based anomaly detection.
- Future-ready for AI-enhanced security.
7. Custom PowerShell Scripts and SDK Tools
For organizations with in-house development teams, creating custom PowerShell scripts using the Dynamics 365 SDK is a cost-effective way to build a tailored Dynamics CRM access checker.
These scripts can query the organization service to retrieve user roles, team memberships, and privilege assignments. They can then generate custom reports, send email alerts for permission changes, or integrate with SIEM (Security Information and Event Management) systems.
Microsoft provides extensive documentation on using the Web API and SDK for security queries. For example, you can use OData queries to retrieve all users with a specific role or check the access level of a particular privilege.
Explore the official SDK guide at Microsoft’s Developer Documentation.
- Full control over access checking logic.
- Can be automated and scheduled.
- Integrates with existing DevOps pipelines.
How to Use a Dynamics CRM Access Checker: Step-by-Step Guide
Implementing a Dynamics CRM access checker is not just about installing a tool—it’s about establishing a process for continuous access governance. Whether you’re using a native Microsoft feature or a third-party solution, the following step-by-step guide will help you maximize its effectiveness.
The goal is to move from ad-hoc access reviews to a structured, repeatable audit cycle that ensures ongoing compliance and security. This process should involve both technical administrators and business stakeholders, especially when defining role requirements and reviewing access exceptions.
Step 1: Define Your Access Audit Objectives
Before running any access check, clarify what you want to achieve. Common objectives include:
- Identifying users with excessive privileges (e.g., system administrator rights).
- Auditing access for compliance with GDPR, HIPAA, or SOX.
- Resolving user complaints about missing access.
- Preparing for a system migration or role restructuring.
Having clear objectives will guide your choice of tool and the scope of the audit. For example, a compliance audit may require detailed reporting and exportable logs, while a troubleshooting session might focus on a single user or record.
Step 2: Select the Right Tool for Your Environment
Choose a Dynamics CRM access checker that matches your deployment model (cloud, on-premises, hybrid) and technical capabilities. Consider factors such as:
- Integration with existing identity providers (e.g., Azure AD).
- Support for bulk operations and automation.
- Reporting formats and export options.
- Cost and licensing requirements.
For small teams, the Power Platform Admin Center or XrmToolBox may suffice. Larger organizations with complex security needs should consider enterprise-grade tools like Inogic or PowerObjects.
Step 3: Run a Baseline Access Audit
Perform an initial audit to establish a baseline of current access rights. This should include:
- A list of all active users and their assigned security roles.
- Team memberships and business unit affiliations.
- Custom roles and privilege modifications.
- Users with elevated privileges (e.g., System Administrator).
Save this baseline for future comparison. Many tools allow you to export the results to Excel or PDF for archival purposes.
Step 4: Analyze and Identify Risks
Review the audit results to identify potential security risks, such as:
- Users with redundant or conflicting roles.
- Over-privileged accounts that don’t align with job functions.
- Orphaned users or inactive accounts with access.
- Missing segregation of duties (e.g., same user can create and approve invoices).
Use the tool’s analysis features—like role comparison or access preview—to dig deeper into high-risk cases.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
Step 5: Remediate and Optimize Access
Based on your findings, take corrective actions such as:
- Removing unnecessary roles or privileges.
- Consolidating redundant roles.
- Reassigning users to appropriate business units.
- Implementing role-based access control (RBAC) policies.
Always follow change management procedures and document all modifications. Some tools offer ‘dry run’ modes to test changes before applying them.
Step 6: Schedule Regular Access Reviews
Access management is not a one-time task. Schedule periodic audits—at least quarterly or semi-annually—to ensure ongoing compliance. Automate reports where possible and assign ownership to specific teams (e.g., IT Security or Compliance).
Integrate access reviews into employee lifecycle processes: when someone joins, changes roles, or leaves the company, their access should be reviewed and updated accordingly.
“Organizations that conduct regular access audits reduce security incidents by up to 70%.” — ISACA, 2023 IT Risk Study
Common Challenges and How a Dynamics CRM Access Checker Solves Them
Even with robust security models, Dynamics CRM environments often face recurring access-related challenges. These issues can lead to operational delays, compliance violations, or data breaches. A Dynamics CRM access checker is specifically designed to address these pain points with precision and efficiency.
Understanding these common challenges helps organizations appreciate the value of proactive access management. Below are some of the most frequent issues and how access checking tools provide solutions.
Challenge 1: Role Proliferation and Complexity
Over time, organizations tend to create numerous custom security roles, leading to a complex and unmanageable permission structure. This ‘role sprawl’ makes it difficult to understand who has access to what and increases the risk of misconfigurations.
A Dynamics CRM access checker solves this by providing a centralized view of all roles and their privileges. It allows administrators to compare roles, identify duplicates, and consolidate overlapping permissions. Some tools even recommend role optimizations based on usage patterns.
- Visual role comparison to detect redundancy.
- Role usage analytics to identify inactive roles.
- Guided role consolidation workflows.
Challenge 2: Inconsistent Access Across Business Units
In multi-tenant or global organizations, different business units may have varying access policies. This can lead to inconsistencies where users in one region have more privileges than their counterparts in another, creating compliance risks.
An access checker with cross-unit reporting capabilities can highlight these discrepancies. It enables administrators to standardize role definitions and ensure uniform access policies across the organization.
“Standardizing security roles across business units reduced access-related support tickets by 45% in a Fortune 500 client.” — Accenture Dynamics 365 Case Study
Challenge 3: Difficulty Troubleshooting Access Issues
When a user reports they can’t access a record or feature, diagnosing the issue can be time-consuming. Administrators often resort to manual checks or impersonation, which is inefficient and risky.
A Dynamics CRM access checker with ‘effective access’ analysis eliminates guesswork. It shows exactly what permissions a user has on a specific record, including inherited access from teams, roles, and sharing rules. This speeds up troubleshooting and reduces downtime.
- Instant ‘Who Can Access This?’ lookups.
- Breakdown of access sources (role, team, sharing).
- No need for user impersonation.
Best Practices for Maintaining Secure Access in Dynamics CRM
Implementing a Dynamics CRM access checker is just the first step. To maintain long-term security and compliance, organizations must adopt best practices for access governance. These practices ensure that user permissions remain aligned with business needs and regulatory requirements.
Security is not a project—it’s an ongoing process. The following best practices, supported by the use of access checking tools, will help you build a resilient access management framework.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
Adopt the Principle of Least Privilege
Always assign the minimum level of access required for a user to perform their job. Avoid giving blanket ‘System Administrator’ roles unless absolutely necessary. Use custom roles to fine-tune permissions and regularly review them for relevance.
A Dynamics CRM access checker helps enforce this principle by identifying over-privileged users and suggesting role adjustments.
Implement Role-Based Access Control (RBAC)
Define standard roles based on job functions (e.g., Sales Rep, Service Agent, Marketing Manager) rather than individual users. This simplifies management and ensures consistency across teams.
Use your access checker to validate that role assignments align with organizational structure and job descriptions.
Conduct Regular Access Reviews
Schedule periodic audits—at least quarterly—to review user access. Include stakeholders from HR and compliance to ensure alignment with employee roles and regulatory standards.
Automate these reviews using scheduled reports from your Dynamics CRM access checker.
Integrate with Identity and Access Management (IAM) Systems
Connect your Dynamics CRM environment with enterprise IAM solutions like Azure AD, Okta, or SailPoint. This enables automated user provisioning, role assignment, and deprovisioning based on HR data.
Access checkers can monitor these integrations for anomalies, such as users retaining access after termination.
Document and Standardize Security Policies
Create a formal security policy document that outlines role definitions, access approval workflows, and audit procedures. Share this with all administrators and enforce it through training and governance.
Your access checker can serve as a validation tool to ensure adherence to these policies.
Future Trends in CRM Access Management and Security
The landscape of CRM access management is evolving rapidly, driven by advancements in AI, cloud security, and regulatory demands. Organizations that stay ahead of these trends will be better equipped to protect their data and maintain compliance.
Future Dynamics CRM access checkers will move beyond static permission audits to dynamic, behavior-based security models. Here are some key trends to watch:
AI-Powered Access Recommendations
Artificial intelligence will play a growing role in access management. Future tools will analyze user behavior to recommend role adjustments, detect anomalies, and predict access needs based on job changes.
For example, if a user is frequently accessing service modules despite having a sales role, the system might suggest adding a service-related privilege or creating a hybrid role.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
Zero Trust Integration
The Zero Trust security model—’never trust, always verify’—is becoming standard in enterprise environments. Future Dynamics CRM access checkers will integrate with Zero Trust frameworks, requiring continuous authentication and context-aware access controls.
This means access will be granted based on user identity, device health, location, and behavior—not just static roles.
Automated Compliance and Audit Readiness
As regulations become more stringent, access checkers will offer built-in compliance templates for GDPR, CCPA, HIPAA, and SOX. They will automatically generate audit-ready reports and alert administrators to potential violations.
These tools will reduce the burden of manual compliance efforts and provide real-time assurance to auditors.
What is a Dynamics CRM access checker?
A Dynamics CRM access checker is a tool or feature that allows administrators to audit, verify, and manage user permissions within a Microsoft Dynamics 365 CRM environment. It helps ensure that users have the appropriate access levels based on their roles and responsibilities, supporting security, compliance, and operational efficiency.
Why is access checking important in Dynamics CRM?
Access checking is crucial to prevent data breaches, ensure compliance with regulations like GDPR, and maintain operational integrity. Without proper access controls, organizations risk unauthorized data access, role conflicts, and inefficient troubleshooting of permission issues.
Can I use a Dynamics CRM access checker for free?
Yes, Microsoft provides free tools like the Power Platform Admin Center and XrmToolBox with basic access checking capabilities. For more advanced features, third-party tools like Inogic Security Manager or PowerObjects Power365 Security offer paid solutions with deeper analytics and automation.
How often should I audit user access in Dynamics CRM?
It is recommended to conduct access audits at least quarterly. Organizations in highly regulated industries may need to perform them monthly or semi-annually. Regular audits help detect and remediate permission issues before they become security risks.
What are the best tools for Dynamics CRM access checking?
Top tools include Microsoft Power Platform Admin Center (free), Inogic Security Manager, PowerObjects Power365 Security, CRM Perfection’s Access Analyzer, XrmToolBox, and emerging AI-powered tools like the DataVerse Security Analyzer. The best choice depends on your organization’s size, complexity, and compliance needs.
dynamics crm access checker – Dynamics crm access checker menjadi aspek penting yang dibahas di sini.
Managing user access in Dynamics CRM is a critical component of data security and operational efficiency. A reliable Dynamics CRM access checker empowers organizations to audit permissions, detect risks, and maintain compliance with ease. From native Microsoft tools to advanced third-party solutions, the right access checker can transform how you manage security in your CRM environment. By following best practices and staying ahead of emerging trends, you can ensure that your Dynamics 365 deployment remains secure, compliant, and aligned with business goals.
Further Reading: